| Track: | GDPR |
|---|---|
| When: | Tue DS-2 |
| Where: | |
| Organizers | Mario Platt Mario Platt |
| Participants | David Cervigni David Cervigni , Jim Newman Jim Newman , Manuel Almeida Manuel Almeida , Mark Regensberg Mark Regensberg , Tony Richards Tony Richards , Vijay Nair Vijay Nair |
| Remote Participants | Abhi Raj Abhi Raj , Lubo Vikev Lubo Vikev , Paul Cutting Paul Cutting , Ryan Farmer Ryan Farmer , Sophie Tonnoir Sophie Tonnoir |
GDPR Patterns are reusable mappings of data journeys across specific threat modelling scenarios.
It aims to support the mapping of data flows and consider security and privacy requirements to meet EU GDPR regulation.
WHY
Threat model diagrams are excellent sources of data mapping as they allow us to ensure a consistent model to assess threats and controls designed to mitigate those threats.
The use of GDPR Patterns permits organizations to risk assess data flows and select technical and organizational measures used to meet security and privacy requirements as set by EU GDPR
What
In order to assess threats to privacy and security and enable organisations to have a standardized approach, there’s the need to define the detail to each step of the patterns. The following steps are to be defined on the data model as standard capabilities:
- Data source
- Categories of individuals
- Categories of Personal data
- Purpose of processing
- Data Security
- Lawful basis of processing
- Data retention
- Data transfer
- Data recipients
What are GDPR Patterns?
They are reusable mappings of data journeys across specific threat modeling scenarios.
The idea is to take the diagram below and map specific scenarios to it.
‘Based on Threat Models?'
Threat models diagrams are perfect sources of data mappings since they already mapped the flows of data (where it comes from and where they go to)
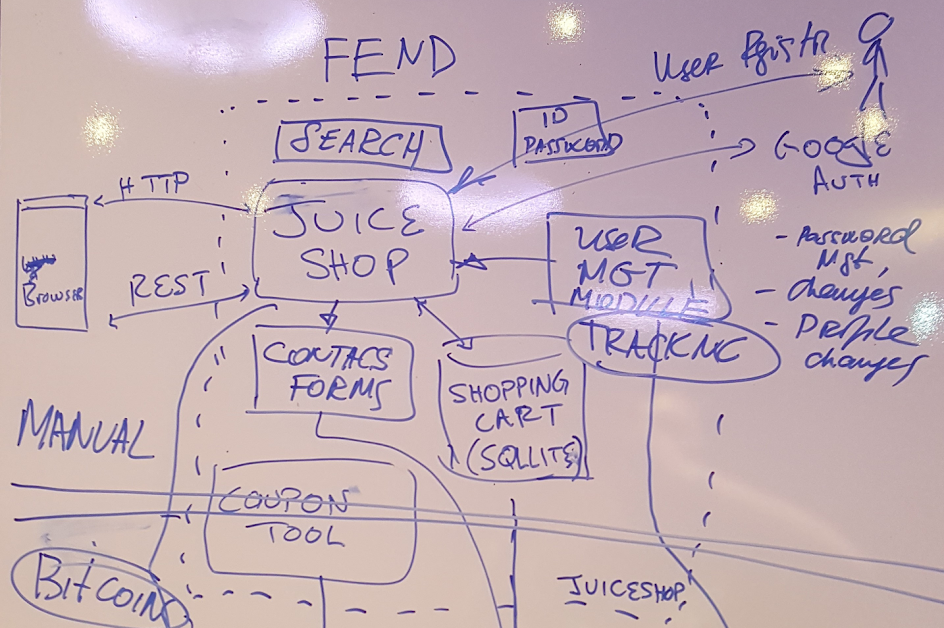
Here is an example of a Threat model created at the last Summit’s Working session on Threat Modeling (on OWASP Juice shop application).
GDPR Pattern driven by Threat Model
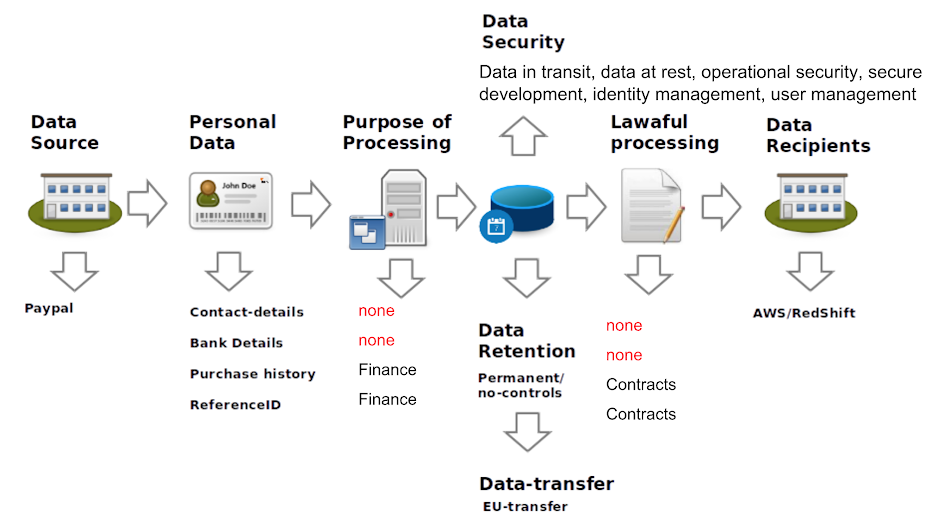
Here is an example of what the ‘GDPR Pattern driven by Threat Model’ mapping looks like when it is done (for a service that regularly fetches data from Paypal and feeds it to AWS Redshift).
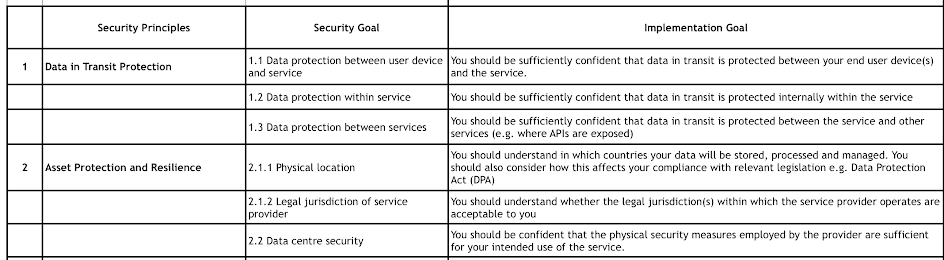
Maping GDPR Appropriate Security Measures
To help with the appropriate security controls, we use this table:
Outcomes
The outcome is to have a standardised data model covering all steps to security and privacy capabilities required, so the model can then be applied and tailored to each organisation and their particular capabilities and risk appetite.
References
OWASP GDPR Patterns
The GDPR patterns is an OWASP Project and all materials created are released under an open source license, allowing for internal and commercial use.
All content is hosted at the https://github.com/OWASP/gdpr-patterns repo
Register as participant
To register as participant add Creating a standard for GDPR patterns to either:
- the
sessionsmetadata field from your participant's page (find your participant page and look for the edit link). - or the
participantsmetadata field from this git session page
Back to list of all Working Sessions